Azure AD connection for the WebModel on IIS
Applies to: viflow (subscription | 9), Azure AD | Article: 1890246 | Updated on 21.05.2024
Initial Situation
Your viflow WebModel is hosted on an internal/external IIS ( Internet Information Services from Microsoft – not in Azure!) and should be connected to the Active Directory on Microsoft's cloud computing platform Azure (Azure AD).
Configuration in Azure
Register new app
- Open the Microsoft Azure Portal from portal.azure.com.
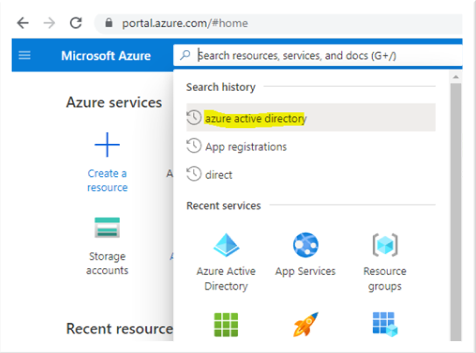
- Open the Azure Active Directory application.
- Under App registrations, click New registration.
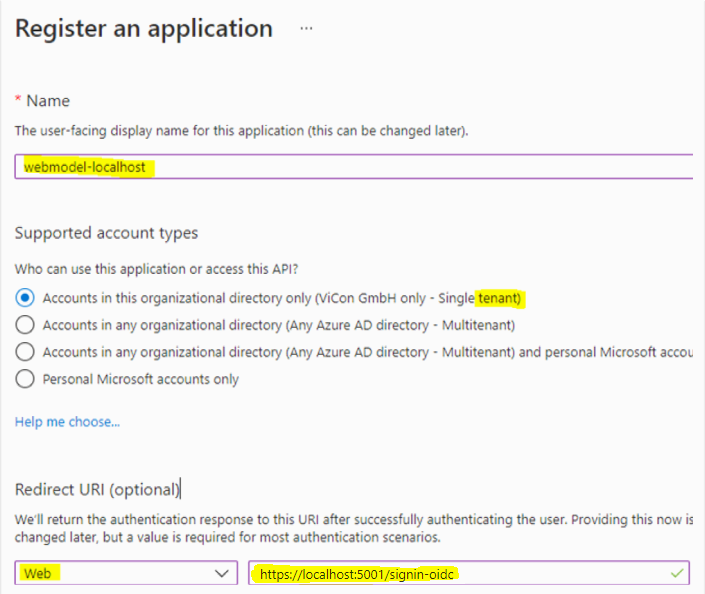 The Register an application window opens.
The Register an application window opens. - Enter a name here and under Supported account types select the Active Directory that is to be connected to the WebModel (here: ViCon GmbH only – Single tenant).
- Under Redirect URI (optional), select Web in the left selection box.
Enter the Redirect URL, which must match the WebModel Server URL.
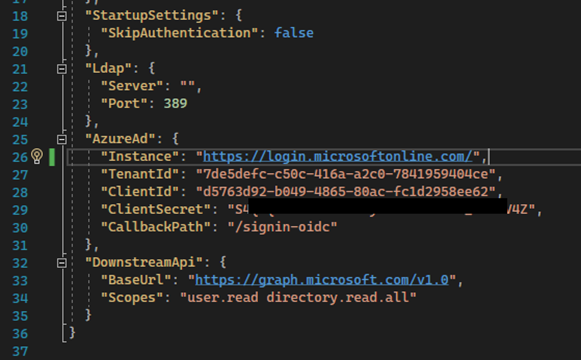
The URL path specification (/signin-oidc) must be identical to the path specification in the appsettings.json file and entered in the settings under AzureAd >> CallbackPath. Then the "Client ID" and "Tenant ID" must be transferred to the WebModel configuration.
- After Client credentials, click Add a certificate or secret.
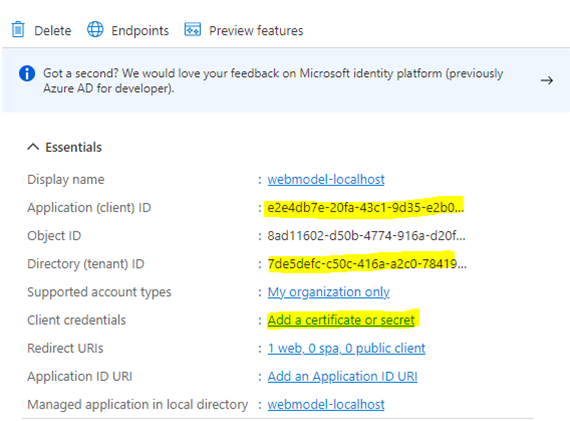
- Select New client secret and transfer this to the appsettings.json file.
Claim Configuration
In the default setting, the Claim OnPremiseSecurityIdentifier is not supplied. This is required by the WebModel to identify users added from the local Active Directory.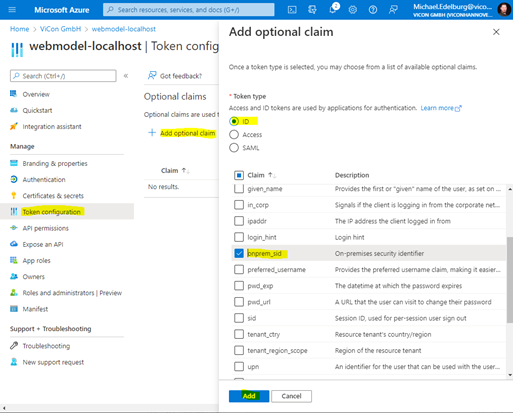
API permissions
The WebModel works with a service account to communicate with the Microsoft Graph API.
A delegation (on-behalf-of) is not readily permitted and therefore the WebModel requires additional permissions.
- Open the Request API permissions window.
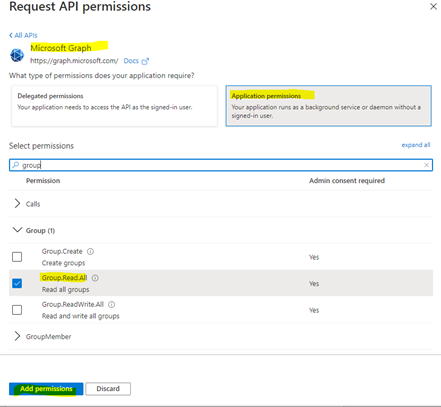
- Under Application permissions, grant the WebModel the following permissions:
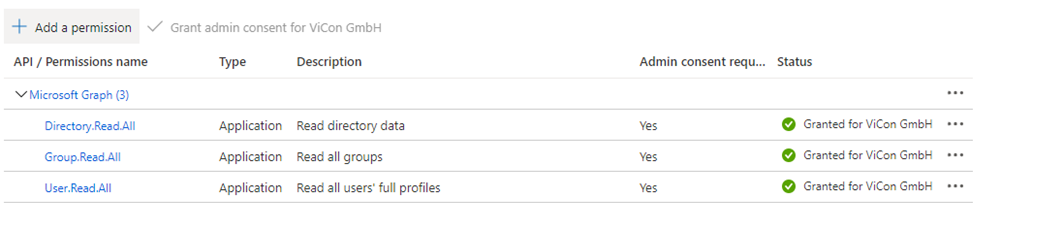 > Directory.Read.All
> Directory.Read.All
> Group.Read.All
> User.Read.All